Things tagged tech:
Did Carnegie Mellon Attack Tor for the FBI?
The behavior of the researchers is reprehensible, but the real issue is that CERT Coordination Center (CERT/CC) has lost its credibility as an honest broker. The researchers discovered this vulnerability and submitted it to CERT. Neither the researchers nor CERT disclosed this vulnerability to the Tor Project. Instead, the researchers apparently used this vulnerability to deanonymize a large number of hidden service visitors and provide the information to the FBI.
Does anyone still trust CERT to behave in the Internet’s best interests?
IPFS
Another take on content centric networking, see also Van Jacobson on CCN and Named Data Networking
Here is the blurb from their website ipfs.io, but the best intro is the video included below …
IPFS is a peer-to-peer distributed file system that seeks to connect all computing devices with the same system of files. In some ways, IPFS is similar to the Web, but IPFS could be seen as a single BitTorrent swarm, exchanging objects within one Git repository. In other words, IPFS provides a high throughput content-addressed block storage model, with content-addressed hyperlinks. This forms a generalized Merkle DAG, a data structure upon which one can build versioned file systems, blockchains, and even a Permanent Web. IPFS combines a distributed hashtable, an incentivized block exchange, and a self-certifying namespace. IPFS has no single point of failure, and nodes do not need to trust each other.
At first glance this is an attempt to get CCN working, in the absolutely simplest way by patching together existing tech. I respect this, and it’s not a diss to say so. Having a working stack to play with will be valuable. However I think the hackyness of this approach will prove to be too much to actually implement, and it will fall back to a complete ground up stack like the NDN folks to get something that is performant and has features like mobile nodes built in.
A 21st-Century Migrant’s Checklist: Water, Shelter, Smartphone
Matthew Brunwasser in the NYT:
“Every time I go to a new country, I buy a SIM card and activate the Internet and download the map to locate myself,” Osama Aljasem, a 32-year-old music teacher from Deir al-Zour in Syria, explained as he sat on a broken park bench in Belgrade, staring at his smartphone and plotting his next move into northern Europe.
“I would never have been able to arrive at my destination without my smartphone,” he added. “I get stressed out when the battery even starts to get low.”
You Can't Walk in a Straight Line—And That's Great for VR
Sarah Zhang in Wired:
Humans, quite simply, suck at walking in straight lines: Give a man a blindfold, and he will walk around in circles. In virtual reality, though, this failing becomes very convenient. People are so bad at knowing where they are in space that subtle visual cues can trick them into believing they’re exploring a huge area when they’ve never left the room—a process called redirected walking.
With VR technology getting ever better, people could one day explore immersive virtual spaces—like buildings or even whole cities—on foot in head-mounted displays. But it’s not very immersive if you end up smacking into a real-life wall. “This problem of how you move around when in VR is one of the big unsolved problems of the VR community,” says Evan Suma, a computer scientist at the University of Southern California.
That’s where redirected walking comes in. People don’t really notice, it turns out, if you increase or decrease the virtual distance they had to walk by 26 percent or 14 percent, respectively. Or shift the virtual room so they see their path as straight when their real path is curved. Or turn the room up to 49 percent more or 20 percent less than the rotation of their heads.
Ironsides
IRONSIDES is an authoritative/recursive DNS server pair that is provably invulnerable to many of the problems that plague other servers. It achieves this property through the use of formal methods in its design, in particular the language Ada and the SPARK formal methods tool set. Code validated in this way is provably exception-free, contains no data flow errors, and terminates only in the ways that its programmers explicitly say that it can. These are very desirable properties from a computer security perspective.
The Ada-Europe 2013 paper (pdf) is pretty readable.
Mills, Hood and FM Synthesis as a Metaphor
Recently while preparing a lecture on the influence of gear on music I puzzled over the formal differences between Chicago’s house and Detroit’s techno. Both owed a lot to the restrictions inherent in Roland’s rigid TR-808 and TR-909 drum machines and the absence of a budget for much more of a set-up. There are so many commonalities that I wondered what the general differences really are. And I don’t seem to be the only one confused. Reportedly, Derrick May thought they were doing house music – until Juan Atkins insisted on the techno tag, which he in turn had borrowed from Alvin Toffler. Researching gear lists, I eventually stumbled upon a device named DX100. It was used by virtually every Detroit producer (including Derrick May: somebody said Nude Photo employs the “Wood Piano” preset) and there were periods where it was the only other sound source in the set-ups of Jeff Mills and fellow minimalist Robert Hood, aside from a TR-909 drum machine. Core lessons learned while adapting to FM have been applied to other synthesizer (and synthesis) models later, shifting the focus of programming from the keyboard-derived approaches of 1970s art rock and fusion to the synthesizer’s modulation matrix.
Love this:
FM taken as a metaphor hints at the problem that in a perception-based production scenario (such as techno’s paradigmatic mode of operation) all parameters are effectively bundled and thus exist in a state of permanent dynamic cross-modulation. Each layer is modulated by all others, mirroring the others, imprinting contours onto each other. Everything is melting into a convoluted perceptual entity where the products of cross-modulation form their own emergent aesthetic layer. No doubt that the stark patterns have obvious rhythmic values, but all the time these also carry other information that wouldn’t exist without a carrier for it to be projected on. Although individual parameters (such as rhythm, pitch or compression ratio) can be described in isolation, such descriptions fail to identify the corresponding functions of their values and movements in context, i.e. their cross-modulated products are missing from the description. The exactly same movement of one parameter may “mean” totally different things in different contexts. One might also recall that outside of scores and measurements, i.e. while listening, we actually never encounter parameters in isolation (no pitch without timbre, no rhythm without duration …): there is no such thing as an independent variable.
Steve Reich stuff
A new game based on Steve Reich’s iconic Clapping Music lets anyone improve their rhythm.
The app on iTunes.
A good interview:
It’s Gonna Rain part II:
And this is just wonderful:
The Untold Story of ILM, a Titan That Forever Changed Film
Wired with an oral history of ILM:
No one wanted Star Wars when George Lucas started shopping it to studios in the mid-1970s. It was the era of Taxi Driver and Network and Serpico; Hollywood was hot for authenticity and edgy drama, not popcorn space epics. But that was only part of the problem.
As the young director had conceived it, Star Wars was a film that literally couldn’t be made; the technology required to bring the movie’s universe to visual life simply didn’t exist. Eventually 20th Century Fox gave Lucas $25,000 to finish his screenplay—and then, after he garnered a Best Picture Oscar nomination for American Graffiti, green-lit the production of Adventures of Luke Starkiller, as Taken From the Journal of the Whills, Saga I: The Star Wars. However, the studio no longer had a special effects department, so Lucas was on his own.
Inside the School Silicon Valley Thinks Will Save Education
Issie Lapowsky at Wired:
AltSchool is a decidedly Bay Area experiment with an educational philosophy known as student-centered learning. The approach, which many schools have adopted, holds that kids should pursue their own interests, at their own pace. To that, however, AltSchool mixes in loads of technology to manage the chaos, and tops it all off with a staff of forward-thinking teachers set free to custom-teach to each student. The result, they fervently say, is a superior educational experience.
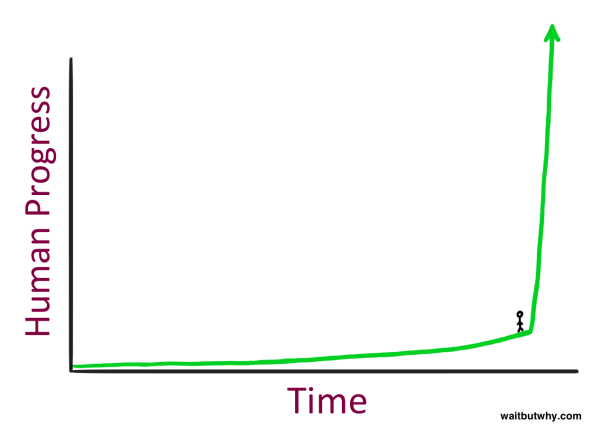
The Artificial Intelligence Revolution
Tim Urban with a decent, if pop-sci, look at the singularity:
What does it feel like to stand here?
Van Jacobson speaks on Content Centric Networking
Nerd out time. Gets really good towards end of part 3.
The Named Data Networking (NDN) project makes use of the CCN (Content-Centric Networking) architecture developed at the Palo Alto Research Center (PARC). In this presentation, Van Jacobson speaks on content-centric networking at the Future Internet Summer School (FISS 09) in Bremen, Germany in June 2009.
Moments That Changed The Movies: Jurassic Park
A look back at Jurassic Park, the groundbreaking decision to create digital dinosaurs, and the impact it had on the future of movies.
Be Still My Breaking Heart
Wisdom from Dan Kaminsky:
First off, there’s been a subtle shift in the risk calculus around security vulnerabilities. Before, we used to say: “A flaw has been discovered. Fix it, before it’s too late.” In the case of Heartbleed, the presumption is that it’s already too late, that all information that could be extracted, has been extracted, and that pretty much everyone needs to execute emergency remediation procedures.
analysis of openssl freelist reuse
Pretty brutal:
About two days ago, I was poking around with OpenSSL to find a way to mitigate Heartbleed. I soon discovered that in its default config, OpenSSL ships with exploit mitigation countermeasures, and when I disabled the countermeasures, OpenSSL stopped working entirely. That sounds pretty bad, but at the time I was too frustrated to go on. Last night I returned to the scene of the crime.
See also: http://article.gmane.org/gmane.os.openbsd.misc/211963
@securityhulk
I love @securityhulk. This ssl mess is making for some lols.
EASY TO RECOVER FROM SSL BUG. JUST REVOKE PRIVATE KEYS, AND ANY DATA SENT THAT EVER TRAVEL OVER SSL SINCE BUG INTRODUCED. EASY PEASY.
24/192 Music Downloads are Very Silly Indeed
Audio nerds: 24-bit/192kHz distribution is better right? Nope:
Monty at xiph.org:
Articles last month revealed that musician Neil Young and Apple’s Steve Jobs discussed offering digital music downloads of ‘uncompromised studio quality’. Much of the press and user commentary was particularly enthusiastic about the prospect of uncompressed 24 bit 192kHz downloads. 24⁄192 featured prominently in my own conversations with Mr. Young’s group several months ago.
Unfortunately, there is no point to distributing music in 24-bit/192kHz format. Its playback fidelity is slightly inferior to 16⁄44.1 or 16⁄48, and it takes up 6 times the space.
There are a few real problems with the audio quality and ‘experience’ of digitally distributed music today. 24⁄192 solves none of them. While everyone fixates on 24⁄192 as a magic bullet, we’re not going to see any actual improvement.
See this fantastic video for a walk through of why stair stepping is a total myth. (Yes you should still record and produce at 24-bit, due to headroom for not worrying about clipping. but mastering (a properly centered mix) to 16bit doesn’t lose anything).
Stephen Wolfram's Introduction to the Wolfram Language
Stephen Wolfram introduces the Wolfram Language in this video that shows how the symbolic programming language enables powerful functional programming, querying of large databases, flexible interactivity, easy deployment, and much, much more.
Intel’s Sharp-Eyed Social Scientist
Natasha Singer in the NYT:
Dr. Bell’s title at Intel, the world’s largest producer of semiconductors, is director of user experience research at Intel Labs, the company’s research arm. She runs a skunk works of some 100 social scientists and designers who travel the globe, observing how people use technology in their homes and in public. The team’s findings help inform the company’s product development process, and are also often shared with the laptop makers, automakers and other companies that embed Intel processors in their goods.
iheartsynths.com - 009: Shawn Rudiman
In 1989, Shawn Rudiman started production work with Ed Vargo as part of the seminal Industrial group T.H.D. (Total Harmonic Distortion). This EBM/Elektro unit became quite popular in the EBM/Industrial music scene of the early to mid 90′s. They released 4 full-length albums, countless remixes and compilation releases on both European and domestic labels. During these formative years, Shawn developed a fascination with vintage music machines. In 1997, he decided to stray from his Industrial-EBM roots to explore the depths of pure rhythm and sounds in Techno music. Rudiman’s all live sets of non-stop, improvised techno became his trademark. His innate understanding of hardware drum machines, sequencers, samplers and synthesizers gave his performances the fluidity and smoothness of any DJ set, but entirely flexible in direction and tempo (well before the introduction of software live applications). These performances gained international attention throughout the Techno community and became the stuff of legend.
Today he resides in the Midwest, still releasing records and remixes. Always a consummate studio enthusiast, Shawn maintains, repairs and builds analog and vintage synthesizers while keeping a busy international touring schedule.